Trufflehog - Stage Failure
This document explains how to identify and resolve TruffleHog findings. TruffleHog is a scanning tool intended to identify potentially sensitive data in your repository, particularly passwords. Passwords for your production environment should never be commited plaintext into your repo. Because TruffleHog checks high-entropy strings and password sets, false positives happen.
List Findings
Go to your pipeline in GitLab. Click on the compliance-check stage, and then on the trufflehog job.
Copy the URL in case you need to open a ticket. If there are any errors, they will be listed towards the bottom of the job log output in JSON format:
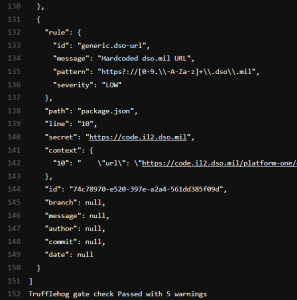
The most useful bits of each finding are "path" and "line" which specify the exact location, "context" which shows that whole line, and "secret" which is only the exact bit that it's complaining about.
"Low" severity rules only issue warnings and do not fail the pipeline. They are only displayed if there are no other higher-severity errors present. These may be used for testing new rules without risk of blocking everyone. One example of this is for hardcoded dso.mil URLs. (This is to discourage accidental cross-Impact-Level linking. Instead use environment variables and relative links/URLs where possible. For example, we populate baseUrl for Cypress testing. Ask for help if you need.)
"Medium" and "High" severity rules are errors and will fail the pipeline.
Download Findings
If there are many findings, it may be helpful to download the whole report file for local viewing in your editor of choice.
Observe the menu items on the right side of the page:
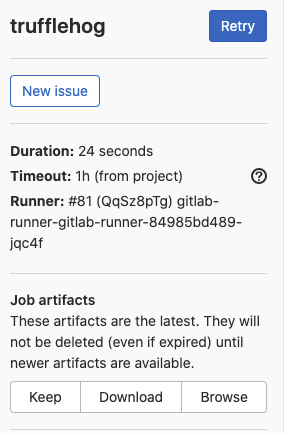
- Select Browse and navigate to the report file.
- Click the json file.
- Download and open in a text editor.
Solutions
- Verify findings are false positives.
- If you find a real credential that snuck in, don't just delete it and hope nobody noticed - Treat that credential as compromised, and change it! (Open a Mission DevOps help desk ticket if you need help with this.)
- For false-positives:
- Some things may be quicker and easier to "fix" yourself by changing your code. (e.g., Does that variable really have to be named password ? This is a very common issue.)
- Do not try to override findings by using trufflehog's inline nosecret annotations - the pipeline job ignores these.
- Since Trufflehog looks for "high-entropy strings" it can trip on all sorts of things like GUIDs, SHA hashes, test data, etc. Open a Mission DevOps help desk ticket for SCA exceptions . For faster service, provide a link directly to your failing pipeline job.