Dependency Check - Recreate Pipeline
Summary
This guide shows users how to recreate a job using their local machine's pipeline, enabling them to test and clean their pipelines independently.
Prerequisites
- Docker knowledge would be helpful, but not needed
- Docker Download and Install
- Docker login in terminal run:
docker login http://registry.il2.dso.mil/- Username: same as P1 username
- Password: Gitlab Personal Access Token
Step-by-Step Guide
- Use the template command to build your Docker run.
Docker run template command:
docker run --rm -it -w /app -v < your_app_repo_path >:/app -v < your_app_repo_path >:/usr/share/dependency-check/data < image_url > sh- Obtain the image from the dependency check job in the pipeline. a. The
<image_url>can be obtained from the job log.${DOCKER_REGISTRY}is set to: http://registry.il2.dso.mil/. Below is an example for the dependency check job: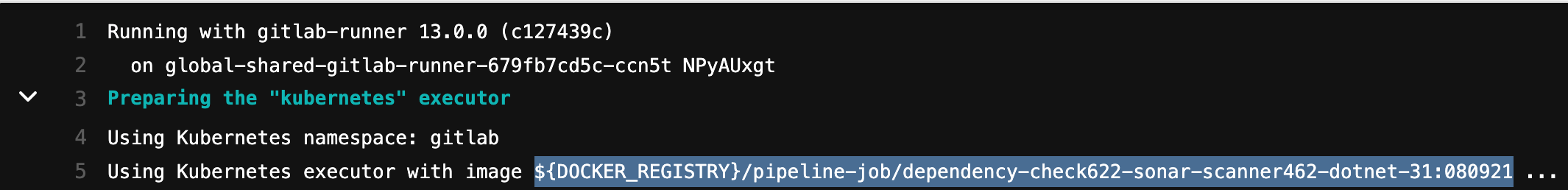 i. Using this example, the image will be: registry.il2.dso.mil/platform-one/devops/pipeline-templates/pipeline-job/dependency-check622-sonar-scanner462-dotnet-31:090621 NOTE: The specific version of the image will change over time. Please verify the current image in the depednency-check job in your current pipeline.
i. Using this example, the image will be: registry.il2.dso.mil/platform-one/devops/pipeline-templates/pipeline-job/dependency-check622-sonar-scanner462-dotnet-31:090621 NOTE: The specific version of the image will change over time. Please verify the current image in the depednency-check job in your current pipeline. - The app that will be used in this example is cpp-world, located locally at /Users/some_user/Workspace/cpp-world/.
- Run the image locally using a Docker run command, similar to the one below:
Sample Docker run command:
# Option 1: Using full path
docker run --rm -it -w /app -v /Users/some_user/Workspace/cpp-world:/app -v /Users/some_user/Workspace/depcheck_data/:/usr/share/dependency-check/data registry.il2.dso.mil/platform-one/devops/pipeline-templates/pipeline-job/dependency-check622-sonar-scanner462-dotnet-31:090621 bashe
# Option 2: CD to the root of project directory
cd cpp-world
docker run --rm -it -w /app - v $PWD:/app -v $PWD:/usr/share/dependency-check/data registry.il2.dso.mil/platform-one/devops/pipeline-templates/pipeline-job/dependency-check622-sonar-scanner462-dotnet-31:090621 sh- You are now in the shell with the terminal with your application in your current working directory. Nothing else is required from the user. However, some things to know and remember include the following:
INFO
A folder called "app" is an arbitrary folder to hold artifacts. The folder will be created if it does not exist. While inside the container, any files created/modified in here will reflect in the directory specificed when exiting the container. The "sh" at the end will bring you to a terminal within the container.
NOTE
The first mount is the actual application itself. The second mount is the CVE Database; it is not necessarily needed, but will speed up subsequent runs.
You can refer to the Docker Manual Page, but the following will summarize what is being used here:
Run commands argument:
--rm # Removes anonymous volumes after exiting the container freeing up resource
-it # Allows user to shell into and interact with the container
-w # Changes working directory within the container
-v # Bind mount a volume allowing sharing between files on your machine to the containerRun the dependency check script.
Dependency check script template:
bashdependency-check.sh -n --scan "${DEPENDENCY_SOURCES}" --format "ALL" --disableOssIndex --enableExperimental --out /app/reports/Search for and obtain depedency sources using the variable
DEPENDENCY_SOURCES. a. To find what the DEPENDENCY*SOURCES are being set to scan, refer to the pipeline-templates Git repo. b. In the example case from cpp,CMakeLists.txt\*\*/\_.cmake.
DEPENDENCY_CHECK_EXTRA: "--enableExperimental"
DEPENDENCY_SONAR_SOURCES: "CMakeLists.txt"
DEPEDENCY_SOURCE: "CmakeLists.txt,**/.*.cmake"Replace the variables with your sources. a. In the example earlier, a full scan would be: --scan "CMakeLists.txt --scan "*/.cmake"
Dependency check example:
bashdependency-check.sh -n --scan "CMakeLists.txt" --format "ALL" --disableOssIndex --enableExperimental --out /app/reports/NOTE
DEPENDENCY_SONAR_SOURCES can be ignored. This var is only used to avoid scanning repo in SonarQube, which SonarQube job is already doing.
When finished, close the container by typing "exit" in the terminal.
Running a Dependency Check on Multiple Targets
Define the targets as parameters with multiple scans such as: --scan "target_1" --scan "target_2" --scan "target_n"
Users should then be able to navigate to where their app resides, and a directory "reports" would have been created with the generated reports in different file formats.
a. From the example earlier, the reports are located under:
/Users/some_user/Workspace/cpp-world/reports/dependency-check.*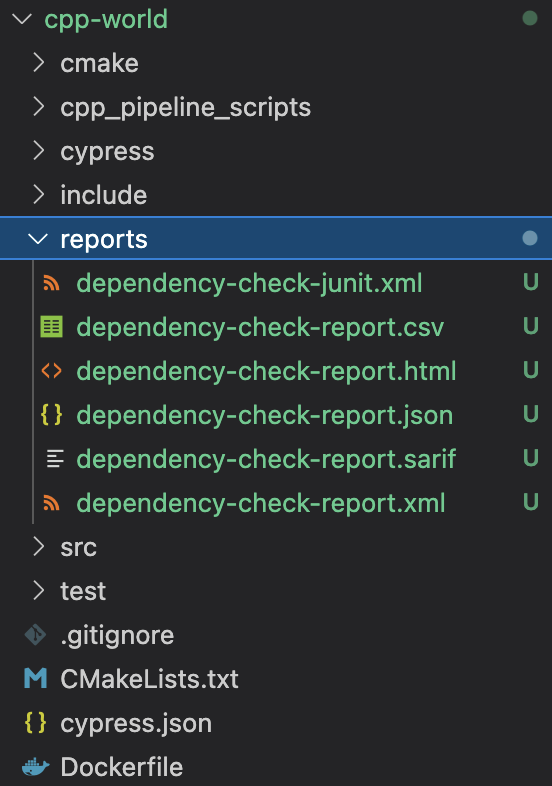
DEPENDENCY_SOURCES by Project Lists
Troubleshooting
Dependency check fails with "Could not perform Node Audit Analysis. Invalid payload submitted to Node Audit API.
a. This occurs when the npm versions are not matched with the dependency check.
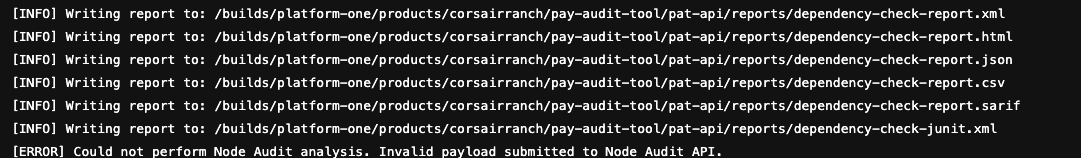
FIX:
- Clone repo locally.
- Upgrade/downgrade to appropriate npm version (6.14.11).
- Run:
rm -rf ./node_modules package-lock.json & npm i- Push back up to repo and rerun pipeline.
FAQs
Will I be able to run this for other pipeline jobs?
This is in progress.