Dependency Checks
General
Insufficient Privileges
Problem
When the pipeline attempts to upload the results of the dependency check to SonarQube, there is an "Insufficient privileges" error. This is caused by a bug in SonarQube that causes the project access template to be removed.
[eval]:1
console.log({"errors":[{"msg":"Insufficient privileges"}]}.queue.length)
^
TypeError: Cannot read property 'length' of undefined
at [eval]:1:66
at Script.runInThisContext (vm.js:122:20)
at Object.runInThisContext (vm.js:329:38)
at Object.<anonymous> ([eval]-wrapper:6:22)
at Module._compile (internal/modules/cjs/loader.js:778:30)
at evalScript (internal/bootstrap/node.js:590:27)
at startup (internal/bootstrap/node.js:265:9)
at bootstrapNodeJSCore (internal/bootstrap/node.js:623:3)Solution
- Open the SonarQube console .
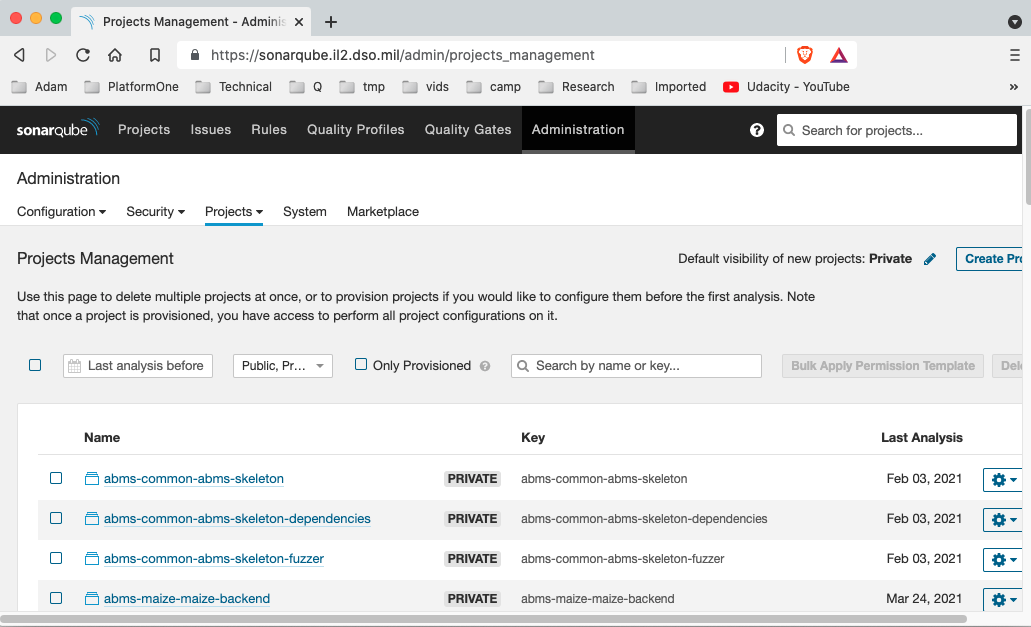
Navigate to Administration → Projects → Management → (Project Name) → Cog to the right → Restore Access.
Back in the project, update the permissions: Project Settings → Permissions → Apply Permissions Template → Default template.
Make sure to add the team's group to the project with Browse and See Source Code permissions.
NPM
Aliases Not Supported
Problem
The dependency check does not support using aliases in package-lock.json.
[WARN] dependency skipped: package.json contain an alias for vue-loader-v16 => vue-loader@16.1.1 npm audit doesn't support aliases
[ERROR] NodeAuditAnalyzer failed on /builds/tron/products/intrinsic/skyhub/skyhub-admin/package-lock.jsonSolution
- Identify aliases using command
grep 'npm:' package-lock.json. The aliases in use should also be made apparent by the error message above.
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ grep 'npm:' package-lock.json
"vue-loader-v16": "npm:vue-loader@^16.0.0-beta.7",
"version": "npm:vue-loader@16.1.1",- Use command
npm ls <alias>to search for uses of the aliased package(s). Its output will denote which packages are using them, and whether they're development or production packages.
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ npm ls vue-loader-v16
skyhub-webapp@0.1.0 /home/ninja/repos/code.il2.dsop/products/skyhub-admin
├─┬ @vue/cli-service@4.5.9
│ └── vue-loader-v16@npm:vue-loader@16.1.1
└── vue-loader-v16@16.0.0-beta.5.4- Manually install the aliased package(s) with
npm install <actual package>. Use--save-devwhen appropriate.
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ npm install --save-dev vue-loader@16.1.1
+ vue-loader@16.1.1
added 4 packages from 6 contributors, updated 1 package, moved 1 package and audited 2005 packages in 23.387s
79 packages are looking for funding
run `npm fund` for details
found 4 low severity vulnerabilities
run `npm audit fix` to fix them, or `npm audit` for details
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ npm ls vue-loader-v16
skyhub-webapp@0.1.0 /home/ninja/repos/code.il2.dsop/products/skyhub-admin
├─┬ @vue/cli-service@4.5.9
│ └── vue-loader-v16@npm:vue-loader@16.1.1
└── vue-loader-v16@16.0.0-beta.5.4
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ npm ls vue-loader
skyhub-webapp@0.1.0 /home/ninja/repos/code.il2.dsop/products/skyhub-admin
├─┬ @vue/cli-service@4.5.9
│ └── vue-loader@15.9.6
└── vue-loader@16.1.1
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$ git diff package.json
diff --git a/package.json b/package.json
index 0b5bfa7..a3cce40 100644
--- a/package.json
+++ b/package.json
@@ -77,6 +77,7 @@
"sass-loader": "^8.0.2",
"ts-loader": "^8.0.4",
"typescript": "^3.9.7",
+ "vue-loader": "^16.1.1",
"vue-loader-v16": "^16.0.0-beta.5.4",
"vue-template-compiler": "^2.6.11",
"webpack": "^4.44.2"
ninja@devops-01:~/repos/code.il2.dsop/products/skyhub-admin$Generic Node Audit Analyzer Package Lock Message
Problem
There is an issue with the package-lock.json file that is not being described in detail. Currently dependency-check does not appear to support lockfile version 3 for package-lock, which may be one of the causes of this issue
[ERROR] NodeAuditAnalyzer failed on /builds/platform-one/products/bullhorn/launchboard/launchboard-be/package-lock.json
[WARN] An error occurred while analyzing '/builds/platform-one/products/bullhorn/launchboard/launchboard-be/package-lock.json' (Node Audit Analyzer).
[INFO] Finished Node Audit Analyzer (0 seconds)
.
.
.
[ERROR] Could not perform Node Audit analysis. Invalid payload submitted to Node Audit API.82ERROR: Job failed: command terminated with exit code 1Solution
(tested and working with npm 8.5.0)
Recreate your package-lock.json by doing the following on your local dev system:
rm -rf node_modules package-lock.jsonnpm iORnpm i --legacy-bundlingto ensure a package-lock.json using package-lock v2.- Commit and push your package-lock.json back to your gitlab repo.
Vulnerable Dependency
Problem
An npm package has a vulnerability.
Solution
- Check to see whether a newer version of the vulnerable package exists at the npm site.
- If so, try to upgrade the npm package that uses the vulnerable package, i.e. the "parent package".
- The parent package can be identified by running
npm list <vulnerable package name>.
Example:
npm list postcss
domino-app@1.0.0 /Users/ninja/repos/code.il2/products/domino/domino-app
├─┬ react-scripts@4.0.3
│ ├─┬ css-loader@4.3.0
│ │ ├─┬ icss-utils@4.1.1
│ │ │ └── postcss@7.0.35 deduped
│ │ ├── postcss@7.0.35 deduped
│ │ ├─┬ postcss-modules-extract-imports@2.0.0
│ │ │ └── postcss@7.0.35 deduped
│ │ ├─┬ postcss-modules-local-by-default@3.0.3
│ │ │ └── postcss@7.0.35 deduped
│ │ ├─┬ postcss-modules-scope@2.2.0
│ │ │ └── postcss@7.0.35 deduped
│ │ └─┬ postcss-modules-values@3.0.0
│ │ └── postcss@7.0.35 deduped- Given the output above, the parent package is react-scripts@4.0.3.
- Return to the npm site to see whether a newer version of the parent package exists. If so, upgrade it.
Up-To-Date Top-Level Dependency Has Vulnerable Sub-Dependency
Problem
The project contains a vulnerable transitive dependency (dependency of dependency), despite having updated top-level dependencies. This can be a security vulnerability.
Solution
- Use overrides to force specific versions of subdependencies: see the npm documentation for more information. (only works for npm v8.30+)
- If unable to use overrides, use the npm-force-resolutions package.
"resolutions": {
"faye-websocket": "^0.11.3",
"immer": "^8.0.1"
},Conan
Dependency File Not Found
Problem
The pipeline cannot find a conan.lock file, which the dependency check job requires.
EXAMPLE:
$ if [[ "$TEMPLATE" == "cpp" && -n "$CONAN_LOCKFILE" ]]; then ## collapsed multi-line command
Error: unable to read lockfile: conan.lock
syntax: conan_dep_converter.sh [<LOCKFILE>]
ERROR: Job failed: command terminated with exit code 1Solution
If the dependencies file has a non-default name (i.e. it's not conan.lock) or is in a non-default location, submit a MDO support ticket . The MDO team will update a pipeline variable to point to the correct file, allowing it to be found and scanned.
Maven
Job stalling or getting 5XX errors from repo.maven.org
Problem
OWASP Dependency check is using Maven Central to rule out false positives. However, if Dependency Check cannot connect to Maven Central, it will repeatedly retry until the job times out. The Central Analyzer runs after the Jar Analyzer. If the job appears to be hung after running the Jar Analyzer (3+ minutes), this is indicative of a connection issue:
[INFO] Finished Jar Analyzer (4 seconds)
[ERROR] Could not connect to Central search. Analysis failed.
java.io.IOException: Finally failed connecting to Central search. Giving up after 7 tries.Solution
Verify Maven Central is down at the Maven Status page.
Re-run your pipeline manually by navigating to the CI/CD section for your project and clicking Run pipeline.
You can also navigate to
https://code.ilx.dso.mil/< your >/< project >/-/pipelines/new.In the prompt for a new pipeline, select the branch you would like to run the pipeline on or leave it at the default, master.
Under the Variables section use the form to add the following variables:
DEPENDENCY_CHECK_EXTRAand--disableCentral, as pictured below.
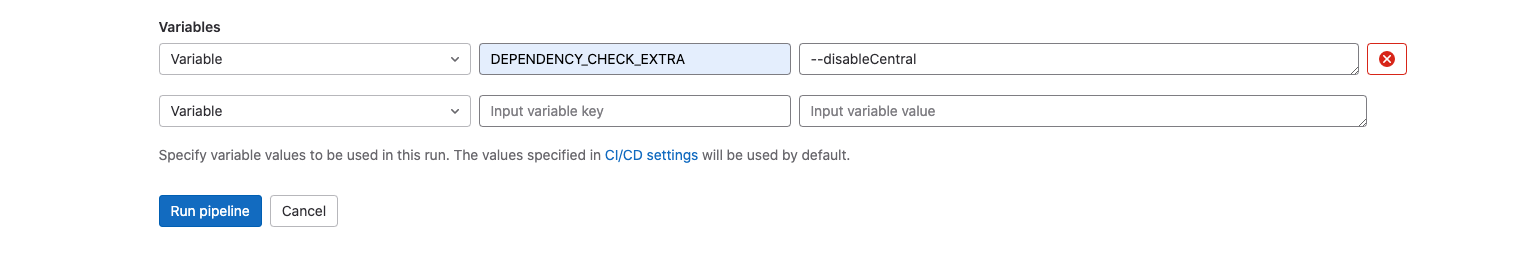
- Click the Run pipeline button.
CAUTION: This workaround will potentially create more false positives. Please open up an SCA ticket to get these resolved as quickly as possible.